home ![]() products
products ![]() pe explorer
pe explorer ![]() feature tour
feature tour
Digital Signature Viewer
Validate the Identity of the Software Publisher
The Authenticode Digital Signature Viewer lets you view the certificate-based digital signature of an executable file, validate the identity of the software publisher, and verify that the signature of a PE file is valid and has been applied properly, and that it wasn't tampered with after it was signed. Furthermore, you have the option to save the signature details in a text file.
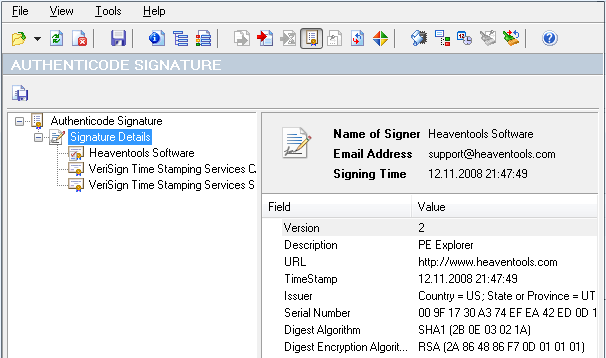
Microsoft Authenticode® code-signing technology is based on the use of a digital signature, which is in turn is based on a digital certificate issued by a trusted third party (a certification authority) that has verified the identity of the software publisher. Code signing lets you know the origin of the code and can protect the code from tampering (if the code is changed, the digital signature is invalidated). Thus, code signing provides two security protections: authentication of the author, publisher, or distributor of the code; and integrity of the code itself.
![]() A great tool for detecting viruses, malware, and other executable nasties, you can use the PE Explorer's Digital Signature Viewer to review and validate the Microsoft Authenticode digital signature, if present, in the loaded executable file. This is a powerful way to verify the publisher and the integrity of the executable.
A great tool for detecting viruses, malware, and other executable nasties, you can use the PE Explorer's Digital Signature Viewer to review and validate the Microsoft Authenticode digital signature, if present, in the loaded executable file. This is a powerful way to verify the publisher and the integrity of the executable. ![]()
Greg Steen,
Microsoft TechNet Magazine
A digital signature is the public certificate plus the value of the signed data encrypted by a private key. When a developer signs the code, it is put through a one-way hash function. This creates a "message digest" (signed hash) of fixed length. The developer's private key is used to encrypt this message digest. The digest is combined with the certificate and hash algorithm to create a signature block. This signature block is inserted into the portable executable file.
Signed Executable File Certificate Viewer
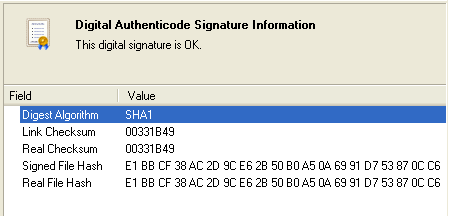
PE Explorer performs a thorough verification process for the digital signature. It first examines the certificate and retrieves the developer's public key. Subsequently, the tool decrypts the message digest using this public key. The same hash algorithm employed to generate the initial message digest is reapplied to the code, resulting in a second message digest (Real File Hash). This second digest is then compared with the original one (Signed File Hash). Additionally, PE Explorer compares the Real Checksum to the value indicated in the header (Link Checksum), as the file checksum field in the optional header can be changed without invalidating the Authenticode signature.
If the two digests match, the signature is deemed valid, confirming that the code remains unaltered since being signed:
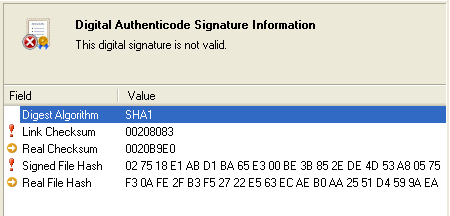
If the two digests (Signed File Hash and Real File Hash) don't match, it indicates that the code has been altered or tampered with in some way. This could be due to the presence of a virus, unauthorized modifications by hackers, or other forms of unauthorized interference. The mismatch between the digests serves as a clear indication of the code's compromised integrity:
View the Certificate Chain
A certificate is a set of data that completely identifies an entity, and is issued by a certification authority (CA) only after that authority has verified the entity's identity. A code signing certificate includes the format of the certificate, the serial number of the certificate, the algorithm used to sign the certificate, the name of the CA that issued the certificate, the name and public key of the entity requesting the certificate, and the CA's signature.
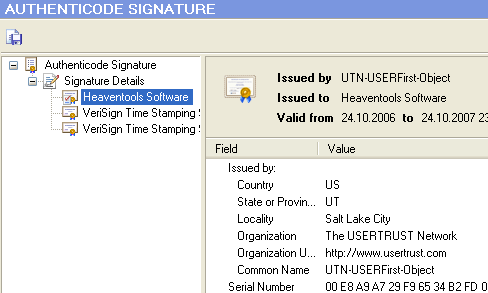
When the software publisher signs the executable file with its private key, you can use the publisher's public key (retrieved from the certificate sent with the software) to verify the publisher's identity.
![]() Download a 30 day trial version of PE Explorer
Download a 30 day trial version of PE Explorer ![]() Buy the Full Version
Buy the Full Version
