Solutions For Malware Analysis And Security Audit
Heaventools provides you with the solutions for disassembly and inspection of executable files that will let you fulfil extensive binary security analysis and binary auditing processes. Enjoy the comfort of being able to have all the necessary tools in one simple, clean interface.
Digital Forensics and Malware Code Analysis
 Malware analysis is quickly becoming a skill that every security professional must have. Reverse engineers within the antivirus and forensic companies face the challenge of analysing a large number of malicious software appearing at an incredible rate.
Malware analysis is quickly becoming a skill that every security professional must have. Reverse engineers within the antivirus and forensic companies face the challenge of analysing a large number of malicious software appearing at an incredible rate.
Though antivirus software is continually getting better, a very significant percentage of malware escapes the automated screening process and manages to wreak havoc on networks. Unfortunately, this percentage is also growing everyday. Antivirus software does little in terms of showing what the malware is doing, and also can mostly only detect previously identified malware, not new malware.
One of the primary tools used in reverse engineering and malware analysis is, and has always been, a disassembler. PE Explorer Disassembler is designed to be easy to use compared with other disassemblers. While as powerful as the more expensive, dedicated disassemblers, PE Explorer focuses on ease of use, clarity and navigation. With this balanced approach, we have succeeded in creating a high-quality disassembler at a reasonable and affordable price point, making it a valuable asset for both professionals and enthusiasts in the field of reverse engineering.
PE Explorer has a rich GUI that allows you to navigate through the various parts of the PE file. You can edit certain parts of the PE file, and its included resource editor is great for browsing and editing the file’s resources. It greatly reduces the time needed to understand the structure of complex malware and reveal the secrets of its design.
Sometimes you have to dig into the file headers in order to determine if there is no trickery happening, particularly when dealing with a potentially harmful malicious binary. If your daily work involves reverse engineering of malware, source code reviews, testing and evaluation of vulnerabilities, PE Explorer can significantly boost your efficiency and enhance the overall quality of your security audit procedures, ultimately saving you valuable hours of time.
Dissassembling the code makes it possible to study exactly how the program works, allowing you to pinpoint potential vulnerabilities. For instance, when reverse engineering spyware on a system, you can determine exactly what type of information the application is attempting to collect, along with its other functionalities.
Other uses of PE Explorer for reverse engineering include uncovering undocumented APIs, porting drivers, and conducting software patch analysis. PE Explorer excels in extracting a wealth of information, including strings, exports, and imports, making it invaluable for malware analysis. The tool enables the detection of meaningful strings throughout the file, providing insights into the executable's functionality. Additionally, if only a scant number of strings are found, there is a strong indication that the code may be malicious in nature.
Digital Signature Viewer lets you examine a certificate-based digital signature of a particular executable file, validate the identity of the software publisher, and verify that the signature is valid, and that an application came from a particular source, and that it wasn't tampered with after it was signed.
Reversing Packed Worms and Trojans
Malicious software authors often use UPX and Upack scramblers to compress their exploits, reducing their size and making them more flexible and adaptable to fit into smaller spaces.
Previously, analysts had to run the executable and dump the packed segments after the file had been completely unpacked in memory.
PE Explorer provides a better solution tailored for the Incident Response and Computer Forensics communities. PE Explorer specializes in handling packed malware executables, even those that have been compressed with UPX and manually modified to prevent straightforward unpacking using the standard UPX uncompressing method.
PE Explorer empowers analysts to effectively examine and analyze such challenging files, enabling a more comprehensive approach to malware analysis and investigation in the face of sophisticated compression techniques.
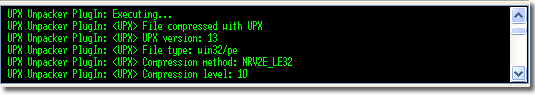
PE Explorer offers robust support for files that have been modified with Upack and various UPX scramblers, including Advanced UPX Scrambler, UPoLyX, UPX Lock, and others. The significant advantage is that users no longer need to be aware of the specific packing method used because PE Explorer can automatically unpack these obfuscated files upon opening them. This feature streamlines the analysis process, allowing users to delve directly into the unpacked contents without worrying about manual unpacking steps, thus saving time and enhancing the efficiency of malware examination and reverse engineering tasks.
PE Explorer exposes entire structure and all resources in suspect file in order to research and reverse engineer it. With PE Explorer, you can rapidly analyze the procedures and libraries a malware executable uses without ever activating the executable itself — a great advantage over debuggers where malicious code needs to be run to be analyzed.
Hex Editor
 Things in the world of malware are not always as they seem. A large part of the malware world evolves around fooling the user. Now that you have a piece of malware in hand, you need the power to look inside it, you need the most commonly used tool — a good hex editor.
Things in the world of malware are not always as they seem. A large part of the malware world evolves around fooling the user. Now that you have a piece of malware in hand, you need the power to look inside it, you need the most commonly used tool — a good hex editor.
FlexHex is specially designed to help you securely view and edit binary files, OLE compound files, logical devices, and physical drives.
Unlike other hex editors, FlexHEX provides full support for NTFS files. This includes full compatibility with sparse files and Alternate Data Streams (ADS) present in files on any NTFS volume.
With FlexHEX, users can conveniently audit their files to identify the presence of Alternate Data Streams and even edit the hidden data contained within them. This feature is particularly useful for forensic analysis, security audits, and tasks that require a thorough examination of NTFS file structures and data streams beyond what traditional hex editors can provide.